- Technology
- Design Security
Design Security
Security Throughout the Product Lifecycle
Security is a complex topic that covers multiple technical disciplines and areas of focus based on the threats a customer is trying to protect against, the sophistication of the adversary they are concerned about, and the environment the end product is deployed in. The Venn diagram below shows the different disciplines that encompass the term "Platform Security" and which AMD invests heavily in.
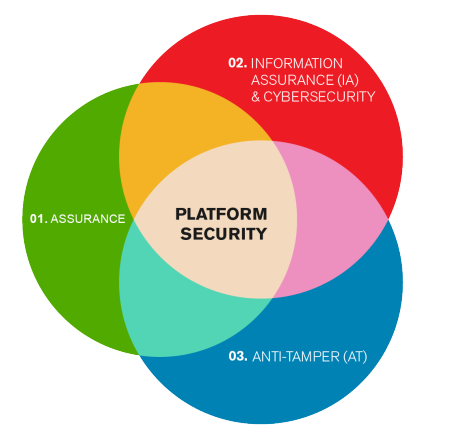
Assurance: Focuses on the known pedigree and heritage of the system solution provided by AMD. Silicon, software, firmware and soft-IP must be "Trojan-free". Supply chain security and risk management are key focus areas.
Information Assurance (IA): Information Assurance is focused on protecting the information, or data, the device is handling or processing. This is done through standard cryptographic techniques (e.g. authentication and encryption) as well as fault tolerant design methods. Fault tolerant design methods ensure that security is not compromised in the face of a fault.
Cybersecurity: While Information Assurance assures all information in all forms of media, Cybersecurity is focused on the protection of information in the cyber domain. This effectively makes Cybersecurity a subset of Information Assurance in most applications.
Anti-Tamper (AT): Focused on protecting the customers’ intellectual property (IP) that is deployed in their product and contained within the device either as hardware or software. Our customers invest heavily in their products, and AMD devices must protect those investments from cloning, reverse engineering or other types of attacks that can extract the IP resident in AMD devices.
As the Venn diagram accurately reflects, there are areas of uniqueness as well as significant areas of overlap between the disciplines. Looking holistically across all disciplines provides the best Defense in Depth approach.
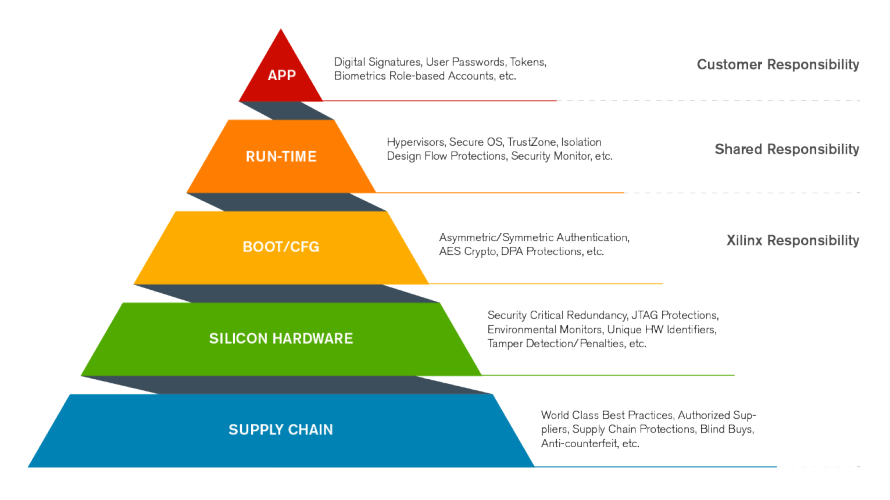
Security must be considered throughout the entire product lifecycle in order to maximize the protection of a system. As an example, developing fault tolerant application level security solutions deployed on a device that does not boot securely, is like building a mansion on a foundation of sand. As can be seen from the pyramid, AMD and their customers have a shared responsibility to ensure the security of a system. It is also important to recognize that no system is completely immune to attack - with enough time, energy, resources and money, any system can be compromised. Security is all about managing risk, and how much investment a customer wants to make to manage that risk.
AMD employs world-class best practices to establish the trustworthiness of its Silicon, Software and Development Tools. An array of countermeasures are integrated into Silicon which aid in protecting against a myriad of attack vectors. The secure boot, or configuration, of our products employ a Hardware Root of Trust with Authenticity, Confidentiality, and Integrity built in.
The device, after booting securely, must maintain the security that has been established. Run-time protections are a shared responsibility between AMD, the customer, and the rich AMD ecosystem.
The base of the pyramid is established to ultimately protect the customer’s end application.
The AMD Xilinx Security Working Group is an annual multi-day FREE event in North America and Europe that brings together AMD customers from all markets, Alliance Partners, government agencies and authorities to discuss the latest security topics.
The unique aspect about this working group is that an NDA is required. This allows us to present roadmap and detailed design information that would not normally be presented in such a forum. ALL PARTICIPANTS WILL REQUIRE A CURRENT NDA.
AMD Xilinx Security Working Group 2024. Save the Dates!
Event #1 - Longmont, CO USA
Date:
October 15-16, 2024 (Unclassified)
October 17, 2024 (Classified)
Location:
Longmont, Colorado AMD Office
>> Registration coming soon!
Event #2 - Washington, DC USA
Date:
November 13-14, 2024 (Unclassified)
November 12, 2024 (Classified)
Location:
Hilton Washington Dulles Airport Hotel
>> Registration coming soon!
Event #3 - Munich, Germany
Date:
December 10-11, 2024 (Unclassified)
Location:
Hilton Munich Airport
>> Registration coming soon!
For more information, feel free to contact your local AMD Xilinx sales representative.
For access to SWG 2023 Presentations please go to our: Design Security Lounge. Please note that an NDA and Lounge access approval is required to obtain these presentations.
Documentation
Cryptographic algorithm validation, via the NIST Cryptographic Algorithm Validation Program (CAVP) is an important aspect of the security solutions provided by AMD. The following table identifies the algorithm, and product, that has been validated with a link to the NIST website.
| Vendor | Program Tier |
Location |
| A2e Technologies Embedded System Design and Custom Application Software Services and Video related IP Cores for AMD Devices. |
Premier | Burlington MA US Guadalajara MX |
| Algotronix, Ltd. Implementation of algorithms on FPGAs, Security and Cryptography |
Select | Edinburgh GB |
| Avnet Avnet is an operating group of Phoenix-based Avnet, Inc. that serves electronic original equipment manufacturers |
Premier | Phoenix AZ US |
| Bottom Line Technologies, Inc. FPGA, board, and system designs for commercial, industrial, and military/IC clients. TS-SCI cleared personnel AMD exclusive regional Authorized Training Partner |
Premier | Columbia MD US Ellicott City MD US |
| CAST, Inc. CAST developes and supports over 100 different popular and standards-based IP cores. |
Elite Certified | Woodcliff Lake NJ US São Paulo SP BR |
| Curtiss-Wright Curtiss-Wright is a technology leader in development of rugged COTS electronic modules and systems for defense & aerospace applications. Curtiss-Wright's FPGA solutions include VPX, XMC, PMC, & FMC. |
Elite | Kanata ON CA Ashburn VA US Newton PA US |
| Cycuity, Inc. HW Security Solution and Verification |
Select | Nashua, NH US |
| DesignLinx Hardware Solutions AMD Premier Partner providing design engineering, coaching/mentoring and learning workshops targeting AMD FPGAs, SoCs, board and system designs for commercial, industrial, and military systems. |
Premier | Nashua, NH US |
| DornerWorks, Ltd. DornerWorks provides expertise and a development plan to help developers create amazing products so that they are free to focus on what they do best. |
Premier | Grand Rapids MI US |
| Extreme Engineering Solutions (X-ES) Extreme Engineering Solutions, Inc. (X-ES) is a leader in the design, manufacture, and support of standard and custom embedded computing solutions. |
Elite | Middleton WI US |
| Fidus Systems, Inc. Electronic product development and consulting services. Capabilities: Hardware, FPGA, Signal Integrity, Embedded Software, PCB Layout, Wireless, DSP, and Mechanical design. |
Premier | Ottawa ON CA Fremont CA US Waterloo ON CA |
| Graf Research Graf Research unleashes innovation by developing ideas into disruptive technologies. |
Premier | Blacksburg VA US |
| Green Hills Software, Inc. | Select | Santa Barbara CA US |
Helion Technology Limited |
Select | Cambridge GB |
| Idaho Scientific LLC Idaho Scientific provides Secure IP and design services tailored to meet DoD Anti-Tamper, Export, and Cyber Security requirements. Additionally, Idaho Scientific provides an inline encryption solution for Zynq UltraScale+ MPSoC/RFSoC as well as Versal. |
Select | Boise ID US |
| intoPIX s.a. intoPIX enables its customers with leading-edge image compression (J2K, TICO,...), security (AES,RSA,...), video transport (AVB, MPEG2-TS,...) and hardware enforcement IP-cores for audiovisual markets. |
Elite Certified | Mont-Saint-Guibert BE |
| Logicircuit, Inc. Logicircuit provides DO-254 compliant IP for AMD devices and also supports the general DO-254 and DO-178C compliance requirements of AMD Aerospace and Defense customers. |
Elite | Alpharetta GA US |
| Mercury Mercury Systems is a global commercial technology company serving the aerospace and defense industry. Headquartered in Andover, MA, the company delivers trusted and secure solutions powering a broad range of mission-critical applications in the most challenging and demanding environments. Additionally, Mercury provides an inline encryption solution for Zynq UltraScale+ MPSoC/RFSoC and Versal. |
Select | Andover MA US |
| Missing Link Electronics, Inc. Turn FPGAs into Programmable Systems with a configurable applications processors running a full GNU/Linux software stack integrated into a pre-validated platform. |
Premier | San Jose CA US Neu-Ulm DE DE |
| Rincon Research Corporation Rincon Research Corporation (RRC) is a world leader of innovative, cutting-edge Digital Signal Processing (DSP) products and solutions targeting the aerospace, defense, and communication industries. |
Select | Tucson AZ US |
| SoC-e SoC-e offers specialized design services and products based on reconfigurable devices. SoC-e is focused on Industrial Networking, Sofware-Defined Radio and VPX Rugged FPGA based systems. |
Elite | Erandio ES |
WIND RIVER SYSTEMS, INC. |
Select | Alameda CA US |
Quick Links
- Product Security Incident Response
- Isolation Design Flow
- content/xilinx/en/products/silicon-devices/fpga/virtex-ultrascale-plus.html
- content/xilinx/en/products/silicon-devices/fpga/kintex-ultrascale-plus.html
- content/xilinx/en/products/silicon-devices/soc/zynq-ultrascale-mpsoc.html
- content/xilinx/en/products/silicon-devices/cost-optimized-portfolio.html
- Design Security Lounge (Documents available under NDA)




